Knowledge Base
- /
- /
 act-ssh for Linux and Mac users – step by step guide
act-ssh for Linux and Mac users – step by step guide
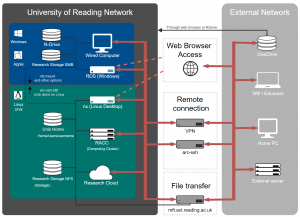
In this article we show a possible approach how to set up a home Unix machine to connect to campus services via act-ssh. It is similar to act-ssh with MobaXterm – step by step guide (it might be usefull to read the MobaXterm article for some extra background explanations). However, beyond setting up the ssh keys, this article is targeted at experienced Unix and ssh users. The commands and the configuration file should be treated just as examples and they might need to be modified to work on your machine. This document builds on what is already described in the instructions for act-ssh, but the goal is to present it as a consistent series of steps, suitable for this particular use case, e.g. we assume that you are working from home, you want to use ssh keys and your openssh version is fairly recent.
Setting up ssh keys – this is necessary to connect to act-ssh and quite basic
We create ssh key pair on the home machine. You can skip this step if you already have the public and private key pair in your ~/.ssh/ directory. We assume that you already have ~/.ssh/ directory in your UoR home directory, if not you need to create it. Then we append the public key to the file ~/.ssh/authorized_keys in our UoR Unix home directory. If you do not have .ssh/authorized_keys in your UoR home directory and the first ‘scp’ line fails, you can continue with the ‘cat’ line, which will create the authorized_keys file if it does not exist. Be careful to not destroy your original authorized_keys file in case if you already have one, and it contains important public ssh keys. Note that it you specify a non-standard name for you private key, you will need to explicitly provide this name to the ssh command. If you have access to VPN, you can also use the simple two line method instead of using MFT, see the instructions for act-ssh.
pawel@homepc:~$ ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/home/pawel/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/pawel/.ssh/id_rsa. Your public key has been saved in /home/pawel/.ssh/id_rsa.pub. The key fingerprint is: SHA256:rAHUFoCc/pxQddysFMZ8Uf/I3AhJeMjNeVIj0JrkhsA pawel@homepc The key's randomart image is: +---[RSA 2048]----+ | . oo=o=+=oX+oo | | +.. Eo= O.B+.. | | . ... o * +oo. | | o . .o = + = | | + .. S. = o| | + o | | . | | | | | +----[SHA256]-----+ pawel@homepc $ scp <UoR user name>@mft.act.reading.ac.uk:/<UoR user name>/.ssh/authorized_keys ./ pawel@homepc $ cat ~/.ssh/id_rsa.pub >> authorized_keys pawel@homepc $ scp authorized_keys <UoR user name>@mft.act.reading.ac.uk:/<UoR user name>/.ssh/ pawel@homepc $ rm authorized_keys
Once this is done we can connect to act-ssh.reading.ac.uk on port 2222. We will be authenticated using the ssh key pair and then we will have to enter the UoR password.
pawel@homepc:~$ ssh qx901702@act-ssh.reading.ac.uk -p2222 ****************************************************************************** * NOTICE TO USERS * * * * Use of this system is restricted to registered members of The University * * of Reading. Unauthorised access is a criminal offence under United * * Kingdom law. * * * * All data stored on this system belongs to The University of Reading and * * may be monitored by authorised personnel. The data on the system may be * * searched at the request of law enforcement or other persons, and may be * * disclosed and used for disciplinary or civil actions and criminal * * prosecution as appropriate. * * * * Use of this computer system constitutes consent to these policies, * * unauthorised users disconnect now! * ****************************************************************************** * Authenticate with with ssh key and then with UoR password * * If you get 'Permission denied' possibly you have not setup your ssh keys * ****************************************************************************** qx901702@act-ssh.reading.ac.uk's password: Last login: Mon Mar 30 15:37:42 2020 from cpc95916-rdng25-2-0-cust250.15-3.cable.virginm.net [qx901702@act-ssh ~]$
From act-ssh we can connect further e.g. to RACC:
[qx901702@act-ssh ~]$ ssh cluster.act.rdg.ac.uk -Y Last login: Mon Mar 30 14:27:43 2020 from act-ssh.reading.ac.uk Welcome to the Reading Academic Computing Cluster (RACC) racc-login.act.rdg.ac.uk is opening a session on one of the login nodes The login nodes can be used for considerate interactive computing and batch job submissions. See https://research.reading.ac.uk/act/knowledgebase/academic-cluster-usage Warning: Permanently added '[racc-login-0-4.local]:33000' (ECDSA) to the list of known hosts. Last login: Sun Mar 29 18:17:27 2020 from racc-login.local Rocks 7.0 (Manzanita) Profile built 13:40 25-May-2019 Kickstarted 14:09 25-May-2019 [qx901702@racc-login-0-4 ~]$
This can also be done in one line, using the ssh jump host option ‘-J’.
pawel@homepc:~$ ssh -J qx901702@act-ssh.reading.ac.uk:2222 qx901702@cluster.act.rdg.ac.uk -Y ****************************************************************************** * NOTICE TO USERS * * * * Use of this system is restricted to registered members of The University * * of Reading. Unauthorised access is a criminal offence under United * * Kingdom law. * * * * All data stored on this system belongs to The University of Reading and * * may be monitored by authorised personnel. The data on the system may be * * searched at the request of law enforcement or other persons, and may be * * disclosed and used for disciplinary or civil actions and criminal * * prosecution as appropriate. * * * * Use of this computer system constitutes consent to these policies, * * unauthorised users disconnect now! * ****************************************************************************** * Authenticate with with ssh key and then with UoR password * * If you get 'Permission denied' possibly you have not setup your ssh keys * ****************************************************************************** qx901702@act-ssh.reading.ac.uk's password: Warning: No xauth data; using fake authentication data for X11 forwarding. Last login: Mon Mar 30 15:43:15 2020 from act-ssh.reading.ac.uk Welcome to the Reading Academic Computing Cluster (RACC) racc-login.act.rdg.ac.uk is opening a session on one of the login nodes The login nodes can be used for considerate interactive computing and batch job submissions. See https://research.reading.ac.uk/act/knowledgebase/academic-cluster-usage Warning: Permanently added '[racc-login-0-4.local]:40518' (ECDSA) to the list of known hosts. Last login: Mon Mar 30 15:43:16 2020 from racc-login.local Rocks 7.0 (Manzanita) Profile built 13:40 25-May-2019 Kickstarted 14:09 25-May-2019 [qx901702@racc-login-0-4 ~]$
Personal ssh configuration file – advanced and optional topics start here
Users can have their personal ssh client configuration file in ~/.ssh/config. We will use this file to automate many aspects of ssh connections via act-ssh to achieve similar effects to those the Windows users enjoy if they follow the MobaXterm instructions. We can select different configuration options for specific hosts or groups of hosts. The following example contains configuration that might be useful for users connecting from home and working on UoR Linux systems.
Host *
ServerAliveInterval 30
ServerAliveCountMax 3
# you might need to create the directory ~/.ssh/controlmasters/
ControlPath ~/.ssh/controlmasters/%l_%r@%h:%p
ControlMaster auto
ControlPersist yes
ForwardX11 yes
ForwardAgent yes
Host act-ssh
HostName act-ssh.reading.ac.uk
User <UoR_username>
Port 2222
# SOCKS proxy tunnel for NX and web browsing
DynamicForward 4444
# example: remote desktop to Windows machine on campus (commented out)
# Localforward <33389> <uor-campus-pc.rdg.ac.uk>:3389
# example: tunnel for NX (redundant example, we use SOCKS instead, commented out
# Localforward <4040> nx.reading.ac.uk:4000HostName act-ssh.reading.ac.uk
Host *.rdg.ac.uk *.reading.ac.uk
User <UoR username>
ProxyJump act-ssh
The first group ‘*’ contains configuration that will be applied to all hosts. The options ‘ServerAliveInterval’ and ‘ServerAliveInterval’ will prevent closing temporarily inactive connections. The three options ‘ControlPath’, ‘ControlMaster’, and ‘ControlPersist’ are here to create and maintain a master connection (ssh multiplexing). This allows to speed up subsequent connections to the same host. Because all subsequent connections will share the same master connection, there will be no need to enter the password again and starting a connection will be very fast as no connection initialization and authentication will be needed. For these options to work you might need to create the directory ~/.ssh/controlmasters/ on your own. Finally, we typically will want to enable X11 forwarding, to be able to run GUI applications on the server and display the application window on the local machine, so we globally set ‘ForwardX11’ to ‘yes’.
The second part of the file contains options for the connection to act-ssh. The first line ‘Host act-ssh’ sets an alias, the name used here could be anything, but using the proper hostname makes sense. The full host name with domain component is defined in the next line. From now on we will use the short name act-ssh and ssh will know that we want to connect to act-ssh.reading.ac.uk using the configuration options set up here. In case you have a different user name on your home machine, it is convenient to specify the UoR user name. In this case we use a nonstandard port, so it is helpful to set ‘Port 2222’, so that we will not have to remember about it each time when making the connection. If we just stop right here, we already have a very convenient set up. From now on, we can connect to act-ssh just by typing ‘ssh act-ssh’, not ‘ssh -p2222 -Y -o ServerAliveInterval=30 -o ServerAliveCountMax=3 qx901702@act-ssh.reading.ac.uk’, and we will need to authenticate to act-ssh only when making the connection for the first time.
pawel@homepc:~$ ssh act-ssh ****************************************************************************** * NOTICE TO USERS * * * * Use of this system is restricted to registered members of The University * * of Reading. Unauthorised access is a criminal offence under United * * Kingdom law. * * * * All data stored on this system belongs to The University of Reading and * * may be monitored by authorised personnel. The data on the system may be * * searched at the request of law enforcement or other persons, and may be * * disclosed and used for disciplinary or civil actions and criminal * * prosecution as appropriate. * * * * Use of this computer system constitutes consent to these policies, * * unauthorised users disconnect now! * ****************************************************************************** * Authenticate with with ssh key and then with UoR password * * If you get 'Permission denied' possibly you have not setup your ssh keys * ****************************************************************************** qx901702@act-ssh.reading.ac.uk's password: Last login: Mon Mar 30 16:27:21 2020 from cpc95916-rdng25-2-0-cust250.15-3.cable.virginm.net [qx901702@act-ssh ~]$ exit logout Shared connection to act-ssh.reading.ac.uk closed. pawel@homepc:~$ ssh act-ssh Last login: Mon Mar 30 16:29:07 2020 from cpc95916-rdng25-2-0-cust250.15-3.cable.virginm.net [qx901702@act-ssh ~]$
If something doesn’t work, or when we are just curious what is happening behind the scenes, we can add the option ‘-v’ for increased verbosity to the ssh command.
Let’s skip the tunneling options for now, and move on to ‘Host cluster’. Here, we define the connection to cluster.act.rdg.ac.uk. The line ‘ProxyJump act-ssh:2222’ will automate connecting via act-ssh as a jump host, so adding -J explicitly will not be needed anymore.
pawel@homepc:~$ ssh cluster Last login: Mon Mar 30 17:06:46 2020 from act-ssh.reading.ac.uk Welcome to the Reading Academic Computing Cluster (RACC) racc-login.act.rdg.ac.uk is opening a session on one of the login nodes The login nodes can be used for considerate interactive computing and batch job submissions. See https://research.reading.ac.uk/act/knowledgebase/academic-cluster-usage Warning: Permanently added '[racc-login-0-4.local]:34232' (ECDSA) to the list of known hosts. Last login: Mon Mar 30 17:06:47 2020 from racc-login.local Rocks 7.0 (Manzanita) Profile built 13:40 25-May-2019 Kickstarted 14:09 25-May-2019 [qx901702@racc-login-0-4 ~]$
In a similar fashion you can add entries for other hosts, also for remote site like JASMIN.
Now let’s discuss the ssh tunnels created in the configuration file, in the act-ssh part. The line ”DynamicForward localhost:4444″ is quite simple and quite powerful. It sets a SOCKS proxy on act-ssh and tunnels it to port 4444 on localhost. Now we can point any SOCKS aware application to use it and connect to campus services via act-ssh. Two examples are the NoMachine Enterprise Client for Linux and Firefox.
In case of NoMachine, you just point it to nx.reading.ac.uk as usual, then click ‘Advanced’, tick ‘Use proxy connection’ and click the corresponding Setting button. There you just tick ‘Manual proxy configuration’, select SOCKS proxy, and point it to localhost port 4444.
In Firefox, we go to Preferences->Network Settings and similar to NX, we set it to ‘Manual proxy configuration’, SOCKS v5, and localhost port 4444. Here it is important to tick ‘Proxy DNS when using SOCKS v5’, so we can use UoR DNS and resolve internal UoR IP addresses (many ACT IP addresses are like that). We might also be interested to use ‘No Proxy for’, and e.g. add *.com (or better not this one as this will include Microsoft sites, e.g. web Outlook, and they will require MFA if connecting from off-campus) and *.co.uk, such that connections to sites like youtube.com, www.netflix.com, or bbc.co.uk will not be unnecessarily routed via the proxy, i.e. via the UoR network. In general, one needs to be careful with this to not route their web browsing traffic via act-ssh when not needed.
The following lines define local port forwarding tunnels, for RDP connections to a Windows desktop and for NX (see Connecting to NX from Outside the University Campus). Most likely we will not need them, as connecting to Windows desktop is not the recommended way of remote working and NX is already configured using SOCKS proxy, but we might use those as examples and create other tunnels as needed.
Storage access
Obviously, we can use act-ssh or (without even setting up two factor authentication for act-ssh) mft.act.reading.ac.uk with any GUI or command line sftp client software. If we want to make it more persistent and transparent, a good option is mounting it with sshfs. Here we are on our personal machine, so we will set it up in the same locations as on UoR systems (but mounting it that way, i.e. for one user, in a shared locations on a shared machine would not be elegant).
pawel@homepc:~$ sudo mkdir /storage/ pawel@homepc:~$ sudo mkdir -p /home/users/qx901702 pawel@homepc:~$ sshfs act-ssh:/home/users/qx901702 /home/users/qx901702 pawel@homepc:~$ sshfs act-ssh:/storage /storage
Alternatively, the directories can be created in user’s home directory and sudo access is not needed.