Knowledge Base
- /
- /
- /
- /
 NX authorization code
NX authorization code
When accessing NX remotely, you may be be asked for an “Authorization Code”. This is a one time code, generated by an authentication app (if you have set one up), or will be sent via email to your university email address.
In this article, you will find key instructions on how to:
- Section 1: Check if you need to apply for access.
- Section 2: Login to NX using a one-time code emailed to your UoR email address.
- Section 3: Set up your authenticator app (optional, but recommended for experienced users).
1. Check if you need to apply for access
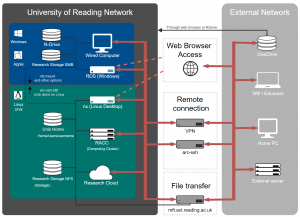
If you are not registered to use https://nx.reading.ac.uk:4443, you will not be granted access when you attempt to login from off-campus. After you enter your UoR password and it is verified, if you are not registered to use the service you will see a message like the following example:
![]()
Assuming you typed in your password correctly, you need to raise a ticket to DTS to be added to the group arc-remote-users (for all Linux/ARC remote access services, unless there is a specific requirement that access is limited to NX only). You should only use your UoR email address or the self-service portal to apply for access, so that we can confirm that the request comes from you. In some cases further checks that the request is genuine might be needed.
When connecting from the UoR campus network, via the VPN or arc-ssh.reading.ac.uk, you will not need a second method of authentication other than your UoR password.
2. Login using one-time email codes
After you successfully authenticate with your UoR password, you will be prompted to enter an authorization code, like in the following example:

If you have not yet set up Google Authenticator for NX or ARC-SSH (see below), you will be sent an email to your university email address with the subject arc-remote.reading.ac.uk off-campus access, which contains your authentication code. Type or copy and paste the 6 digit code you find in the email into the “Authentication code” box. If you mistype the code, you will be sent a new code to use instead of the original code. Note that the code is valid only for this particular authentication prompt and that it times out eventually. It is best to have your email client already opened and be ready to copy the code. If you do not manage to enter the email code in time you will have to enter your username and password again and then you will receive another email with a new code, which you will be expected to enter.
New users of UoR Linux systems can stop here and just use the email codes to login. However, we recommend that all users, once they have some experience in using our systems, set up a more robust two-factor authentication. The method of authentication following in the next section will replace the email code authentication.
3. Set up Google Authenticator
Once Google Authenticator is configured, by running the setup script below in a command window on NX, prompting for the Google Authenticator verification code will replace prompting for and sending email codes. We recommend to replace email codes with Google Authenticator codes because email is not a reliable way to deliver the authentication code on time. There is a risk you might not be able to login when there is some delay with your email delivery. Note the authentication code for NX is the same as the one as used by arc-ssh so if you have already setup arc-ssh you just use those codes.
The general idea of Google Authenticator is as follows: A secret key is placed in a file on the server. On the ACT systems using this method of authentication the file is located at /var/authenticator/<UoR username>/.google_authenticator. The secret key is also transferred to your mobile device when you scan the QR code (you can also achieve this by copying the secret key by hand, or by using the URL to have the QR code displayed in a web browser), and it is stored in the authenticator app. The secret key plus the current time is used to generate time based verification codes. Comparing those verification codes confirms the identity of the device used to authenticate the connection.
You need to install the Microsoft Authenticator app (this is recommended because it is already used with other UoR services) or the Google Authenticator app on your phone. Both the Google and Microsoft apps are compatible with the Google Authenticator service and the following setup steps are the same in both cases. Once the app is installed, run the configuration script below on arc-ssh. The script will produce a QR code that allows to transfer the secret to your mobile device without having to copy the long code manually. In the app, you will need to scan the QR code displayed on the computer screen. If you have problems with the QR code displayed in the text console, you can use the provided URL, or you can copy the secret key as text. The configuration script is modified to store the Authenticator files locally on arc-ssh, not in your shared home directory, so that setting it up on arc-ssh will not affect how you login to other UoR services. Note that every time you run the script, a new secret code is created and the old one is overwritten. That means that each time you run the script, you need to scan the QR code again.
In the following example, we first login to https://nx.reading.ac.uk:4443 using the email code as the two-factor authentication method. Once we are connected we run the script which replaces the email codes with Google Authenticator codes in a mate terminal
ab123456@nxnode3:~$ /usr/local/bin/google-authenticator Warning: pasting the following URL into your browser exposes the OTP secret to Google: https://www.google.com/chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/ab123456@arc-remote.reading.ac.uk%3Fsecret%3DFOO3L3KAPLYPSA7WG3D6YSJBAA%26issuer%3Darc-remote.reading.ac.uk

Your new secret key is: FOO3L3KAPLYPSA7WG3D6YSJBAA Your verification code is 843654 Your emergency scratch codes are: 27275024 33549668 50127586 91900156 28478521
It makes sense to save a copy of the emergency scratch codes. You can use them in case you are not able to login with the standard, time based, verification codes.
The URL, the QR code and the secret key contains the same secret, they should not be revealed, printed or stored in a file.
Now, when you login, you will be prompted for the verification code from the app, not for the code sent by email:
In case you want to revert to using email codes, you will need to remove the file /var/authenticator/<UoR login>/.google_authenticator.
Note the code is for arc-remote.reading.ac.uk as it can also be used on arc-ssh.reading.ac.uk and other remote service